Anonymous tricked into installing Trojan

Update: Anonymous reacts to Symantec Trojan report
Anonymous supporters who willingly used their PCs to participate in the group's Distributed Denial of Service (DDoS) attacks may have unknowingly handed over their personal e-mail and banking information in the process. In January 2012, an unnamed attacker took Slowloris, one of the DDoS attack tools popular with Anonymous supporters, and rigged it to include the Zeus Trojan. The individual copied and pasted an original Anonymous Pastebin entry offering the actual tool and replaced the download link with his own infected version. It just so happened that this post went viral among Anonymous supporters. To this day, it is still being shared on Anonymous blog posts and via Twitter.
If you haven't heard of Zeus, it's a Trojan horse that steals banking information via two methods: man-in-the-browser keystroke logging and Form Grabbing. First identified in July 2007, Zeus is spread mainly through drive-by downloads and phishing schemes, and its various variants have already infected hundreds of thousands of PCs. Now it looks like Zeus has been used to steal financial data from Anonymous supporters.
The story begins on January 19, 2012, when authorities raided Megaupload, and Anonymous hackers retaliated by taking down DOJ, RIAA, MPAA, Universal Music websites, among others. That day, Anonymous released a list of several different DDoS attack tools under a guide referred to as "Tools of the DDoS trade" and "Idiot's Guide to Be Anonymous." Under "Operation Megaupload," supporters were urged to download one of the tools, which would enable them to contribute to the DDoS attacks with their own computers.
In the following weeks, the compromised DDoS tool may have also been used in attacks on several U.S. government websites to protest the government's support of the Anti-Counterfeiting Trade Agreement (ACTA) and against Syrian government websites. Since the modified Slowloris link was on the list, countless people who thought they were simply supporting Anonymous' mission were actually compromising their own financial security.
Security firm Symantec has the details:
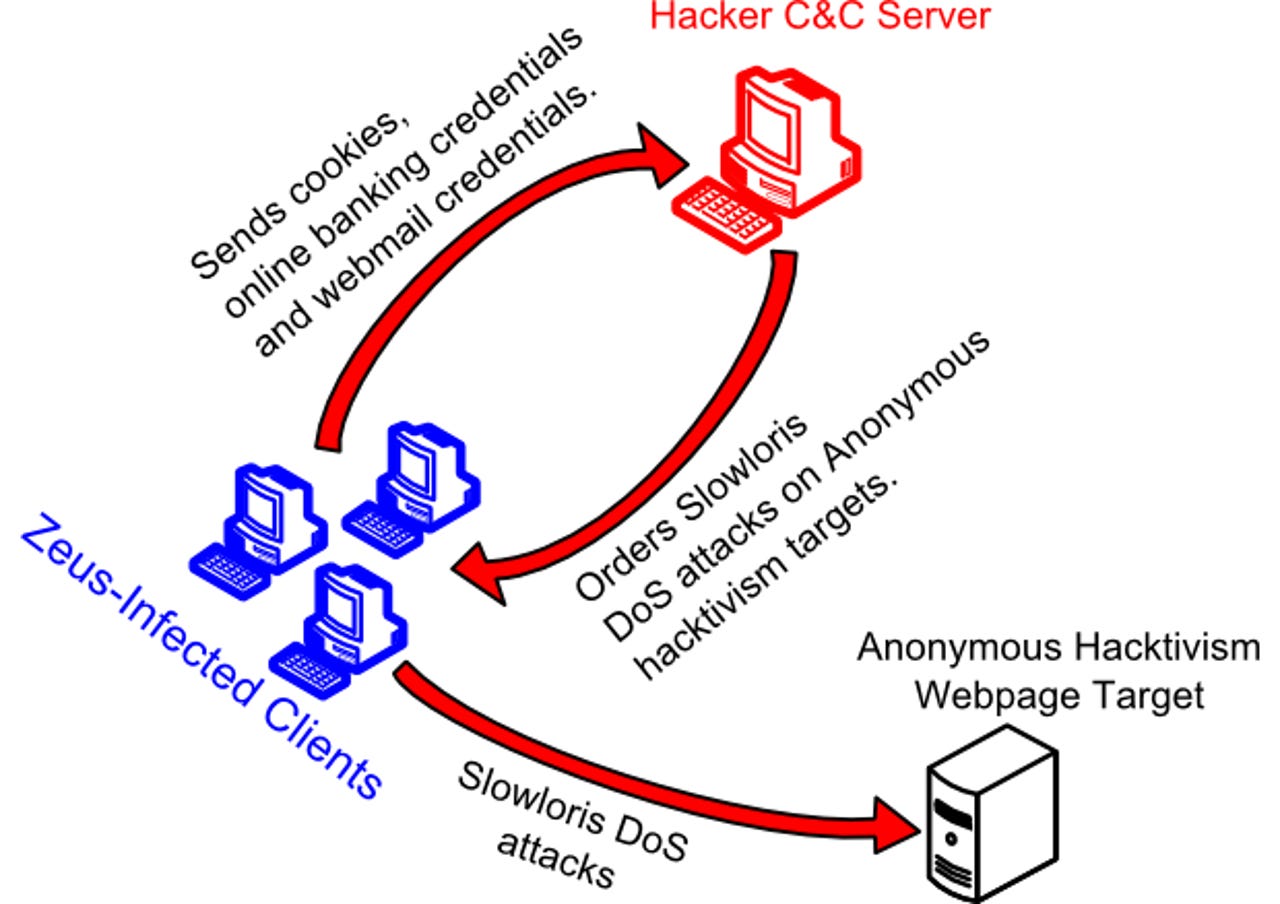
An attacker took a popular PasteBin guide, used by Anonymous members for downloading and using the DoS tool Slowloris, and modified it. In this modified version, the attacker changed the download link to a Trojanized version of the Slowloris tool with matching text. Later that same day, a separate Anonymous DoS guide was posted on PasteBin which included links to various DoS tools. Slowloris was included in this list of tools—the Trojanized version copied from the modified guide.
Once downloaded, installed, and executed, the infected version of Slowloris uses the Zeus botnet client to send login credentials and cookies to the criminal's C&C server. In typical Trojan fashion, the botnet also orders the Slowloris tool on the infected user's computer to attack Anonymous targets, ensuring that the victim still sees the tool do what he or she expects it to.
It's not clear how many Anonymous supporters used the infected Slowloris, so there's no way to gauge how many were (or still are) unknowingly transmitting their own bank account data to a remote server. Security companies have previously warned Internet users backing Anonymous not to participate in the DDoS attacks because they are breaking the law. Now, Symantec says they "may also be at risk of having their online banking and email credentials stolen."
Update: Anonymous reacts to Symantec Trojan report
See also:
- Anonymous launches 'Operation Global Blackout', aims to DDoS the Root Internet servers
- Weekend Anonymous attacks bring down major websites
- How Anonymous took down the DoJ, RIAA, MPAA and Universal Music Websites
- Anonymous is not attacking Facebook today
- Profile of a failed Anonymous attack
- How to try to stop DDoS Attacks