As many as 200 computers belonging to government ministries, a nuclear safety agency and a regional petroleum company are under the control of sophisticated espionage software that has ties to attackers who have previously penetrated RSA, the Dalai Lama's network, and dozens of high-level government systems, researchers said.
The discovery, disclosed by members of Dell SecureWorks at this year's RSA security conference in San Francisco, underscores the endurance of attacks known as APTs, or advanced persistent threats. One of the malware samples used in the espionage campaign was first detailed in a 2010 report (PDF) that revealed a massive spy network that targeted the government of India, the Dalai Lama and other Chinese dissidents located in Tibet. A later report from antivirus provider Trend Micro said the "Enfal" malware, aka the "Lurid Downloader," infected at least 1,465 computers in 61 countries. The campaign discovered by SecureWorks also used a second malware family known as "RegSubsDat" that was first identified in 2009.
Three of the IP addresses used by the servers that controlled the compromised systems observed by SecureWorks also overlapped with addresses that hosted servers used in attacks last year on RSA. The attackers used their access to RSA's systems to steal highly sensitive data related to the company's two-factor SecurID authentication tokens that 40 million employees use to access corporate and government networks. The IP addresses belong to the China Beijing Province Network's autonomous system 4808, which researchers say has long been a hotbed for espionage-related malware.
"I'm a little surprised that when their infrastructure and malware was outted they didn't switch all their tactics and tools," Joe Stewart, director of malware research at SecureWorks, told Ars. "It speaks to the level of risk they must feel they're facing to just brazenly go about business as usual."
It also speaks to the lack of coordination among those who defend government and corporate networks against snoops and other outsiders. Too frequently, different researchers assign vastly different names to the same pieces of malware and don't share intelligence about domain names and IP addresses used in attacks they observe. That makes it hard for defenders to build up a collective body of knowledge about common threats. To address the shortcoming, SecureWorks's 17-page report (PDF) devotes more than four pages to the cataloging of cryptographic hashes used to digitally fingerprint files associated with the underlying malware used in the latest attacks.
Unlike most financially motivated hacks that target anyone with a computer connected to the Internet, APTs single out specific organizations identified in advance as possessing data that's considered valuable. That makes APTs significantly harder to defend against, since the attackers who carry them out will continue their campaigns until the target is successfully penetrated.
SecureWorks' researchers observed the infected machines as recently as last week after gaining control of several of the domain names compromised machines contacted after becoming infected. By "sinkholing" the command and control servers, the researchers could observe the IP addresses of the affected systems. The 100 to 200 separate computers were located in Vietnam, Brunei, Myanmar, Europe and the middle east. In addition to government ministries, a nuclear safety agency, and businesses including the petroleum company, victims also included an embassy located inside mainland China. SecureWorks didn't identify any of the victims by name.
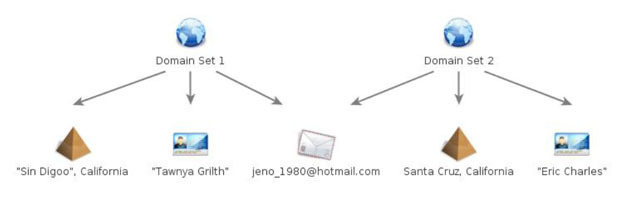
Where in the world is Sin Digoo, California?
Virtually all of the domain names used in the campaign uncovered by SecureWorks were registered by someone using the e-mail address jeno_1980@hotmail.com. Many of those domains were listed as belonging to someone named Tawnya Grilth from the fictional or misspelled town of Sin Digoo, California. The Hotmail e-mail address was also used to register socialup.net, a site that offers blackhat SEO, or search engine optimization, services. Someone called Tawnya has repeatedly promoted the site on message boards, suggesting that in addition to registering domains used in corporate and international espionage, the person may have enjoyed more than a passing interest in blackhat SEO.
The same Hotmail address and Sin Digoo location were used to register other domains and to make inquiries on software developers' forums about code relating to using Windows programming interfaces, which are often of interest to people who write malware. Fingerprints belonging to the same person or group were also found in a user database for rootkit.com, a website where both whitehats and blackhats gathered to discuss the class of highly stealthy malware. The database was leaked onto the 'Net last year following the dramatic breach of the site as part of a larger attack by Anonymous on principals of HBGary.
In all, the attacks observed by SecureWorks involved dozens of active and defunct command and control servers and the trojans identified by the researchers are only a small fraction of the malware they say is being used in online espionage campaigns.
"Collaboration between government, espionage malware victims, and the computer security industry must improve to better defend against this undercurrent of activity that threatens to undermine an already weakened economy in countries around the world," their report concludes.
Listing image by Photograph by images.cdn.fotopedia.com
reader comments
25