Iranian computers are being targeted by malware that wipes entire disk partitions clean, according to an advisory issued by that country's Computer Emergency Response Team Coordination Center.
Dubbed Batchwiper, the malware systematically wipes any drive partitions starting with the letters D through I, along with any files stored on the Windows desktop of the user who is logged in when it's executed, according to security researchers who independently confirmed the findings. The reports come seven months after an investigation into another wiper program targeting the region led to the discovery of Flame, the highly sophisticated espionage malware reportedly designed by the US and Israel to spy on Iran. Wiper, as the earlier wiping program is known, shared a file-naming convention almost identical to those used by the state-sponsored Stuxnet and Duqu operations, an indication it may have been related, security researchers said.
Separate wiping malware known as Shamoon wreaked havoc on some energy-sector computers, including 30,000 workstations operated by Saudi Aramco, the world's largest oil producer. Unlike Wiper, the Shamoon code base is considered rudimentary, raising the possibility that it was developed by hacktivists or other amateur coders. Batchwiper, which gets its name because its destructive payload is contained in a batch file, also appears to be rudimentary.
"Despite its simplicity in design, the malware is efficient and can wipe disk partitions and user profile directories without being recognized by antivirus," the Iranian CERT advisory, which was published on Sunday, stated. "However, it is not considered to be widely distributed. This targeted attack is simple in design and it is not any similarity to the other sophisticated targeted attacks."
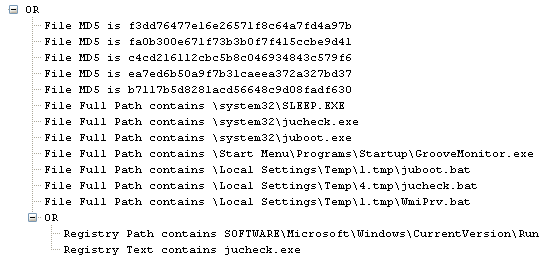
An analysis from researchers at security firm AlienVault shows that the malware is able to remain active even after a machine is rebooted. It does this by adding a registry entry. The RAR archive dropper is named GrooveMonitor.exe, presumably to disguise it as a legitimate Windows Office 2007 service. GrooveMonitor.exe then drops additional files named juboot.exe, jucheck.exe, SLEEP.EXE, and WmiPrv.exe.
According to Symantec, the batch file is programmed to wipe drives only on certain dates, with the next one being January 21. Previous dates listed in the file include December 11, 12, and 13, suggesting the malware campaign may have been active for the past week and may already have inflicted damage.
It remains unclear how Batchwiper is spreading. Possibilities, AlienVault researchers said, include the use of USB drives, malicious insiders, Spear Phishing campaigns or "probably as the second stage of a targeted intrusion."
Researchers at Kaspersky Lab have also weighed in on the new malware.
"There's no connection to any of the previous wiper-like attacks we've seen," Roel Schouwenberg, a senior researcher at Kaspersky Lab, wrote. "We also don't have any reports of this malware from the wild."
Report updated to add details from Kaspersky.
Listing image by pictolang.com
reader comments
23