
While Android 4.2 Jelly Bean was only an incremental update for the mobile operating system, it introduced a ton of much-needed security improvements. As we touched upon in our exhaustive review, Google stepped up its game by implementing native security features that perform functions like scanning side-loaded apps before they're installed to run them against other known cases of malware, and offering SMS confirmation to notify the user if an application wants to send out a text message.
The addition of these features is a step in the right direction, but there were already a wealth of third-party security applications available in Google Play. Companies like Lookout, AVG, and Avast all base their livelihood on protecting Android users (and some iOS users, too) from break-ins. The plethora of third-party apps got us wondering: will Google's inclusion of its own security features render those third-party applications obsolete?
Third-party apps
Let's start with Lookout, a mobile security app with a majority of its customers using the Android platform. This app contains most of the features that Google offers natively in Android 4.2, as well as a basket full of other features that aren't available in the Android OS. There's a free and premium version of the security suite: the free version protects against malicious software, provides data backup and restoration, and helps locate the phone if it's misplaced. The premium version requires a $2.99 monthly subscription and gives you access to several other features, like the ability to remotely lock a phone from a website. But where Lookout really hopes to keep its edge against Google's native security implementations is with its Mobile Threat Network, which the company says constantly analyzes apps from Google Play and third-party markets and scans for new mobile threats that arise globally.
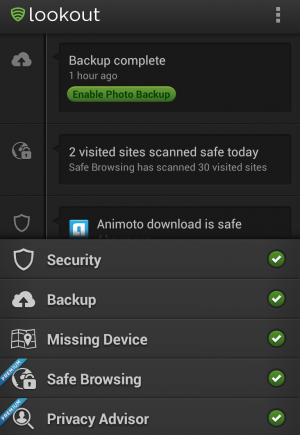
Lookout is confident that its Mobile Threat Network will help the company maintain its relevance even as Google increases Android's security offerings. "The effectiveness of [this] type of product is fundamentally dependent on how complete that data set is," Senior Security Project Manager Derek Halliday told Ars. "We've been looking at the apps across Google Play and alternate markets for more than a few years now and we're pretty confident that our data set is the most comprehensive out there."
The company's app checker works a lot like Android's in that it scans a database of known, harmful apps, but it also runs threats against its own curated library of blacklisted apps and sources that it has been compiling since its inception. Lookout acquires this data by "decomposing" apps and utilizing pattern matching to find other apps that might match that malicious code. "That's something we're going to be continually growing," adds Halliday. "There's a lot more that the data set can power."
Abheek Gupta, senior project manager at Lookout, elaborated on this, adding that with this source of information, the company can work faster against rising threats. "As a company with the expertise, we can actually respond to many things faster than bigger companies and platforms can," he said. "We're able to provide that quick turnaround time for features, for capabilities, for protection."
AVG, which started out by protecting desktop PCs, also offers a suite of security products for Android handsets, including a free version, a pro version priced at $9.99, and a tablet-specific edition. The company's goal has been to take its core technology from the PC side and bring it to mobile handsets. Its Android apps perform real-time scans against previously known malicious data, just like on the PC. AVG also offers a file scanner that can actually look at files stored on SD cards or that have been downloaded to the phone via e-mail or other means, and a settings scanner that looks at the user's security settings to help them choose the best options for their individual usage. Additionally, the pro version offers the ability to locate a lost or stolen device, back up and restore data, and eliminate tasks that slow down the phone.
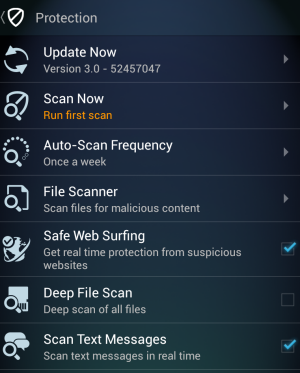
Tony Anscombe, senior security evangelist at AVG, explained that antivirus companies have an advantage with their link scanner technologies because, although Google has its own list of malicious apps it works to actively combat, the antivirus companies actually scan things in real time. "We're not looking at blacklisting, but behavioral characteristics," Anscombe told Ars. "Google will have that blacklist of known issues and bad apps, whereas the security companies will be doing that in real time and looking at the behavior of the apps in real time."
Regardless, both companies do agree that Google's inclusion of native security features is ultimately the best thing for the consumer. "All signs point to the fact that they're actively engaged in understanding what the actual issues are in the Android ecosystem," said Halliday. "Android is a huge moving target and [Google is] doing a lot to move that platform forward. From a security standpoint, it looks like [Google is] being very attentive and reactive to the issues that are affecting most users."
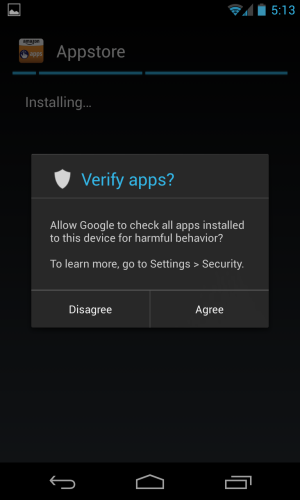
It has. Back in February, Google announced its bouncer-like, server-side app scanner for the Google Play store that would attempt to stop harmful applications from making it past the approval process. The company took this same philosophy it was applying to the applications asking for entrance into the marketplace and implemented it natively into the Android code for side-loaded applications. "We want to make sure that this awesome security feature extended to all sources of applications on the device," said Hiroshi Lockheimer, vice president of engineering for Android, during a phone call with Ars. "We felt that security is a universal thing—it shouldn't be a Play-store-only feature. We wanted to protect our users across the board."
Like Lookout and AVG, Google has been accumulating background knowledge on a variety of malicious applications. "We know what sort of APKs exist and we can apply those same techniques to applications from the Web," Lockheimer explained. When an app is then side-loaded—apps like Amazon Marketplace or Swype, for instance—Google sends up the signature information to the server to determine if it's safe to install or not. And like all of the other apps featured in the Google Play store, Lockheimer mentions that the user "can decide whether they want to participate in this service or not, and it's freely available to them as long as they run 4.2."
So while third-party virus scanners offer a multitude of features that Android doesn't yet natively offer—like the ability to locate a device—is there any reason to use those apps for their virus and malware scanning abilities? Windows users, for example, don't necessarily need to install any third-party applications because Microsoft's native Security Essentials is lightweight and super easy to use. It was also, at one point, detecting 30 percent more malware than third-party companies, according to Jon Oberheide, CTO of Duo Security, which offers two-factor authentication for iOS and Android.
Oberheide believes that, as in the example of Windows, there really is no reason for Android owners to invest in a third-party mobile virus scanner, because the manufacturer—Google, in this case—is the only one that can actually hit malware where it hurts. "Lookout can only do very limited things because it doesn't have root access to super-user privileges," Oberheide told Ars. "It can only sort of hook in where it's allowed it to, whereas Google can do whatever they want. They control the platform and they can do much more comprehensive protection."
Oberheide added that although Google has had a lot of bad press for malware apps infiltrating Android handsets, the company has obviously been working on building infrastructure to prevent this from happening. Google's bouncer-like system, for instance, works well as a gatekeeper, and though it's only in its beginning stages, Google is going to actively continue to improve it to ensure that its Android users are protected from harm. Lockheimer echoed this point earlier, when he said, "We work on features that we believe are generally useful to the general public, and things that we think should belong in the platform. It was important for people to feel secure when they use their devices and feel safe when they're downloading and installing applications."
Keep in mind that any mobile operating system has its vulnerabilities; Android's have just been among the most widely publicized. Any user who is utilizing an Android handset should be aware of the perils that they can come across, but they shouldn't run scared. Google's security features are enough to protect them from common threats. On the plus side, if they're looking for a few added features that aren't yet available natively in Android—like the ability to locate the handset should it get lost or the ability to scan files downloaded via e-mail—there are certainly apps for that. Also, users who haven't yet been able to upgrade to Android 4.2 Jelly Bean can use a third-party security app in the interim and carry it over to their updated handsets in the future with all of those extra features.
In the end, just being aware of potential threats can do wonders. "Some very simple education of users can go a long way," concluded Oberheide.
reader comments
36