Paula Broadwell, the biographer and reported mistress of CIA director David Petraeus, appears to have been a subscriber to the "private intelligence" firm Stratfor—and that means that her Stratfor login account and its hashed password were hacked and released last year by Anonymous.
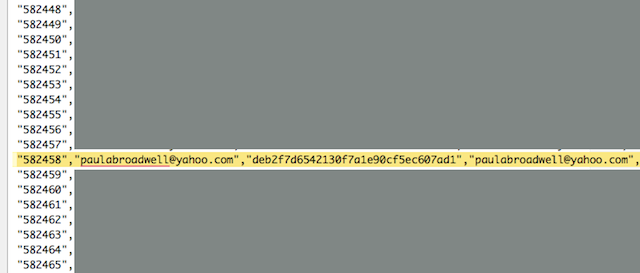
The Stratfor hacker, who the US government says was Chicago-based Jeremy Hammond, obtained a complete roster of all corporate client accounts. These were released online in a massive file called stratfor_users.csv. Inside that file appear the details for one paulabroadwell@yahoo.com, whose hashed password is listed as "deb2f7d6542130f7a1e90cf5ec607ad1."
It's not clear whether the leak was meaningful—Broadwell's Stratfor password and her actual Yahoo e-mail password might have differed—but the prevalence of password reuse raises the possibility that hackers could have accessed her Yahoo e-mail or perhaps even the Gmail account she allegedly used to correspond with Petraeus.
BuzzFeed speculated that this might have happened and that Anonymous might have had access to Broadwell's Yahoo account, at least. Security researcher Robert David Graham casts a skeptical eye on the story, though, noting that Broadwell's password was a good one that resisted obvious dictionary attacks. Graham had broken it, however, using a brute-force attack that simply tried every letter and number combination in existence, running 3.5 billion combinations per second against the password until he found it.
Given that any hacker in the world could have done this since the data leaked, and given that the password might well have been unique to Stratfor, and given that Broadwell wasn't especially in the public eye until last week, Graham concludes that it's unlikely Anonymous was somehow sitting on a gold mine of information about the Petraeus affair.
Still, the whole episode is a textbook illustration of how hashed password leaks occur, how easily the hashes are broken, and how important it is not to reuse passwords across accounts. (Seriously, don't do it if the accounts are in any way important.) If you're looking for an in-the-news example with which to encourage your dad not to set all his e-mail and banking passwords to "Elvis," look no further.
Oh—and remember to drive home the importance of both uniqueness and length. Uniqueness alone can save one leak from compromising all of one's accounts, but unique passwords can still be brute forced if they are short enough. In this case, Broadwell's eight character password took 17 hours to crack; but because "time to crack" rises dramatically as password length increases, even another digit or two can make all the difference. As Graham noted, "Had her password been one character longer, I wouldn't have cracked it."
For more information and tips to secure yourself, see our feature on password cracking from earlier this year.
reader comments
41