A password-cracking campaign against players of the popular game Guild Wars 2, combined with account log-in problems, generated more than 8,500 support requests over the weekend, company officials said, adding that the account take-over attacks were in part aided by compromised credentials siphoned from an unknown fan site that was recently hacked.
Officials with Guild Wars 2 developer ArenaNet recently began the practice of proactively e-mailing customers when someone logs into an account from a new location. They're also advising users to choose long, random passwords that are unique to their accounts and to check e-mail only from trusted devices. From Friday to Sunday, officials said they received about 8,500 support requests related to hacked accounts or blocked accounts. By Monday, the company's support team helped 2,574 players with hacked accounts get back into the game. It also restored service to another 2,867 players with other blocking login issues.
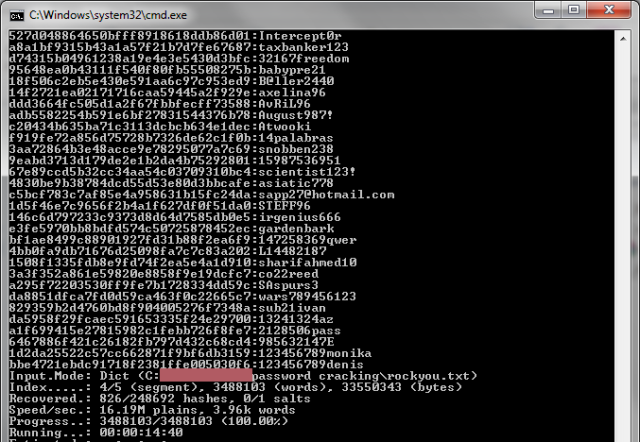
"If you don't want your account hacked, don't use the same email address and password for Guild Wars 2 that you've used for another game or web site," officials wrote over the weekend. "Hackers have big lists of email addresses and passwords that they've harvested from malware and from security vulnerabilities in other games and web sites, and they're systematically testing Guild Wars 2 looking for matching accounts."
The compromised sites include an unidentified Guild Wars related fan site that ArenaNet officials said recently warned of a breach of its account database. "That's important, but just one of many apparent breaches of other games and web sites that hackers have been collecting email addresses and passwords from," they added.
The warnings come amid a wealth of anecdotal evidence pointing to an ongoing campaign, possibly by people located in China, to gain unauthorized access to Guild Wars 2 player accounts. On Thursday, an employee of Norway-based security firm Norman ASA recounted receiving an e-mail warning that someone used her details to attempt to log in to her Guild Wars 2 account just one day after it was created.
"It's been just over a week since the game launched, and I’ve now had 10 e-mails detailing attempts to access my account from China," the unnamed Norman employee wrote. "I live in Europe. Thankfully, creators ArenaNet make players confirm login locations via e-mail, so all these hacking attempts have failed."
Guild Wars 2 user forums are filled with threads like this one and this one, which tell similar tales. Online games such as World or Warcraft have long been hotbeds for account takeovers because the in-game assets such as gold and weapons can be sold online for real-world money. Accounts themselves are often sold wholesale.
"Uhm.. WTF!?" one Guild Wars 2 player wrote. "This is... frightening. I’ve barely owned the game for a day and already I’ve got chinese hackers after my stuff?"
ArenaNet officials should be applauded for being upfront about the attacks and providing effective advice for choosing passwords that aren't susceptible to cracking attacks. Chief among that advice is picking a long, randomly generated password that isn't used on any other site. That means, at a minimum, a password with eight characters—although 13 or even more is better—that's generated using a password management program such as PasswordSafe or LastPass. The password should use both numbers and capital and lower-case letters. If the password won't be entered with a limited keyboard, adding punctuation and other symbols is also a good idea.
The part about the need for passwords to be unique to a given site is crucial. The Norman employee said the e-mail address and password used for her compromised account was also used two years ago to leave a comment on a website that later got hacked. The anecdote exposes a fundamental truth about compromised passwords that Ars explains in much greater detail here, namely that the Internet never forgets. Once a password has been compromised anywhere, it likely will live on forever in thousands of password lists that hackers use to gain unauthorized access to accounts.
ArenaNet officials didn't respond to e-mails seeking comment for this article.
This article was updated on September 10 at 13:07 to correct the number of accounts affected and to make clear support requests also involved blocked accounts.
Listing image by Guildwars2.com
reader comments
81