Attack code that exploits a privacy information leak introduced in the latest version of Firefox is available online, making it easy for malicious websites to gather detailed information about users' browsing history unless they downgrade to the previous Mozilla release.
As previously reported, Mozilla officials took the unusual step of temporarily removing Firefox 16 on Wednesday, just one day after its release. Company officials warned that a security hole introduced in the release "could allow a malicious site to potentially determine which websites users have visited and have access to the URL or URL parameters." They went on to say there was no evidence the vulnerability was being exploited by real-world attackers.
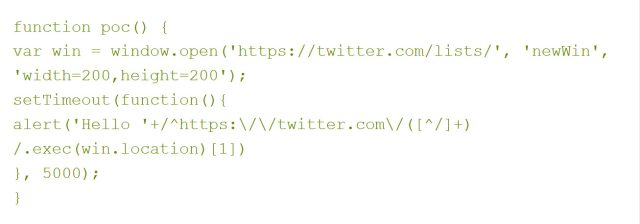
Mozilla's advisory came several hours after a JavaScript blogger published a post titled "Firefox knows what your friends did last summer." In it, he reported some curious behavior in the latest version of the open-source browser, where an undefined value is converted to a string inside a native function. In short order, he was able to take advantage of his discovery to fashion proof-of-concept code that forced Firefox 16 to identify a visitor's Twitter handle whenever the user was logged in to the site. The eight-line code sample takes about 10 seconds to reveal the username, and it wouldn't be hard for developers to expand on that code to create attacks that extract personal information contained in URLs from other websites.
Until a few years ago, Firefox, Internet Explorer, and most other browsers suffered from a decade-old weakness that allowed websites to extract a visitor's browsing history by manipulating the cascading style sheet technology that causes visited links to appear in a different color than addresses that haven't been visited. In late 2010, security researchers reported that YouPorn and 45 other sites actively exploited the weakness to pilfer visitors' browsing habits. Jon Oberheide, CTO of mobile firm Duo Security, said the vulnerability in Firefox 16 is likely more serious because it doesn't require attackers to use a predetermined list of sites to make guesses about where a victim has browsed.
"It appears that this vulnerability allows access to the full URL of an entry in the browser history, without actually having to know that full URL in advance," he told Ars. "In the proof of concept, you can see he's doing a regex match to grab the user's twitter username."
Update, Oct 12, 1:57 PDT: In an e-mail sent more than 24 hours after this article was published, a spokesman for Mozilla wrote: "The flaw allowed access to the URL of windows or frames to which the attacker has a reference only—generally the ones that the attacker opened. It does not access 'history', only what the browser is doing at that moment."
Jeff Williams, a web application security expert and CEO of Aspect Security, e-mailed Ars with additional analysis of the vulnerability.
"Looks like Firefox introduced a code change that allows a malicious webpage to run some JavaScript that can access the 'location' (the URL bar) of windows," he wrote. "So attackers can abuse this by using JavaScript to open other windows to protected websites. Then that JavaScript can access the URL and give it to the attacker. This should result in an 'Error: Permission denied' message, but FF16 allows it."
Williams continued:
"This is most effective when the attacker can find a website that redirects to a URL with something sensitive in it—like your Twitter username. So although it sounds like a history-stealing attack, it really isn't. It allows access to URL's that might contain sensitive information."
As of 11:25 California time Firefox 16.0.1 for desktops had been pushed out to computers belonging to several Ars employees. Readers who are still using Firefox versions 15.0.1 or 16 should expect the update to install in the next few hours. Those who don't want to wait can expedite the update by selecting Help from the menu and then selecting About Firefox. Version 16 should be eventually be available here, although at 11:25 that link was still pushing version 15.0.1. Mozilla has released Firefox 16.0.1 for Android on Google Play.
Story updated to add details about Firefox 16.0.1 and analysis from Jeff Williams.
Listing image by Aurich Lawson
reader comments
42