Black Hat explains fake password reset e-mail sent to 7,500

Earlier today, thousands of Black Hat attendees received a very dubious password reset e-mail with a suspicious URL. The e-mail had the subject "Your admin password" and claimed to come from "BlackHat 2012" but was really sent out by someone with the e-mail address "gleach@itn-international.com."
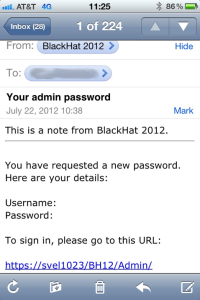
The e-mail, which was sent to some 7,500 security experts, looked something like this (also pictured on the right):
This is a note from BlackHat 2012.
You have requested a new password. Here are your details:
Username:
Password:To sign in, please go to this URL:
https://svel1023/BH12/Admin/
Talk about a poor phishing attempt (includes a username and password in a plaintext e-mail, asks you to sign in to a website that isn't Black Hat, and doesn't even try to spoof a Black Hat e-mail address). Were the phishers really hoping that because the username and password were missing, the recipients would try to log into the fake website with their correct credentials? Nah, I think someone was just really bored (after all, the link isn't even a proper URL).
Conference organizers quickly apologized for the mishap, which they blamed on a volunteer, in a blog post titled Black Hat USA mass reg email. Here's the crux of their explanation:
The link provided in the email is to an onsite host on our registration network. We have reviewed the server logs, we know the user, host, and have spoken with the volunteer who has emailed each of you this morning.
Our most valued assets at Black Hat are our delegates and their privacy. We work very hard to maintain that. We want everyone to come to Black Hat to learn and enjoy their time without fear of having their personal or professional information compromised. We are happy to report there are no signs of compromise.
The email this morning was an abuse of functionality by a volunteer who has been spoken to. This feature has since been removed as a precautionary measure.
The good news is that Black Hat wasn't hacked (although I wouldn't be surprised given the potential glory) and attendee e-mails were not stolen. This is a perfect example of the risk you take when you outsource your accountability.
While this type of faux pas can indeed happen to anyone, it is particularly embarrassing for an organization like Black Hat. After all, they just allowed a fake e-mail to try to dupe some of the world's top security gurus.
For those who aren't aware, Black Hat Briefings is a security conference with attendees that include federal agencies, corporations, and hackers (of course). Black Hat USA 2012 began Saturday (yesterday) and runs until Thursday. Our very own Ryan Naraine is on the scene and will be bringing you news and analysis throughout the week.
See also:
- Obama: Cyber attack serious threat to economy, national security
- FBI: US losing hacker war
- Richard Clarke: China has hacked every major US company
- Former Pentagon analyst: China has backdoors to 80% of telecoms
- US and China test response capabilities via cyber war games
- Defense expert: US should hire hackers to conduct cyberwarfare