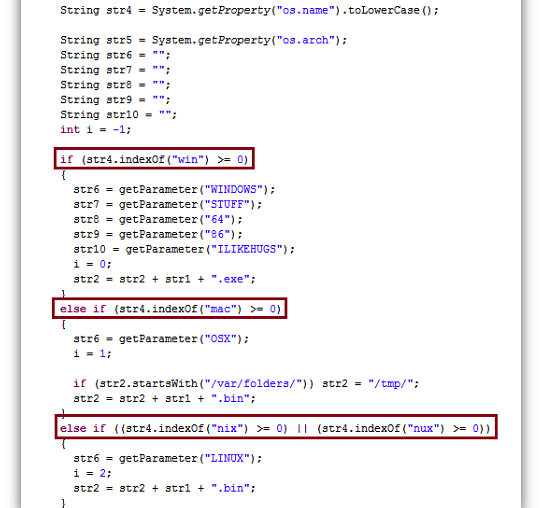
Security researchers have found a live Web exploit that detects if the target is running Windows, Mac OS X, or Linux and drops a different trojan for each platform.
The attack was spotted by researchers from antivirus provider F-Secure on a Columbian transport website, presumably after third-party attackers compromised it. The unidentified site then displayed a signed Java applet that checked if the user's computer is running Windows, Mac OS X, or Linux. Based on the outcome, the attack then downloads the appropriate files for each platform.
"All three files for the three different platforms behave the same way," the researchers wrote in a blog post. "They all connect to 186.87.69.249 to get additional code to execute. The ports are 8080, 8081, and 8082 for OS X, Linux, and Windows respectively."
The growing popularity of Macs has ushered in a rash of new malware attacks that target the platform, most notably the Flashback menace, which infected more than 650,000 machines. Reports of real-world attacks on the Linux operating system are less common, but they do happen, most notably those from last year that infected some of the top Linux developers. But single attacks that have the ability to infect any one of the three OSes are even more rare.
Surprisingly for such an advanced exploit, it was unable to infect modern Macs unless they were modified to run software known as Rosetta. The software allows Macs using Intel processors to run applications written for Macs using PowerPC processors, which were phased out about five years ago. Rosetta is no longer even supported on Lion, the most recent version of OS X.
The F-Secure post said the hacked website and the server used to control infected machines have been reported.
Update
Dave Kennedy, a security researcher and president of TrustedSec, contacted Ars Technica to say the code pictured in this article was taken from an open-source toolkit he wrote.

reader comments
61