The Flame espionage malware targeting Iranian computers contains code that can completely hijack the Windows update mechanism that Microsoft uses to distribute security patches to hundreds of millions of its users, security researchers said Monday.
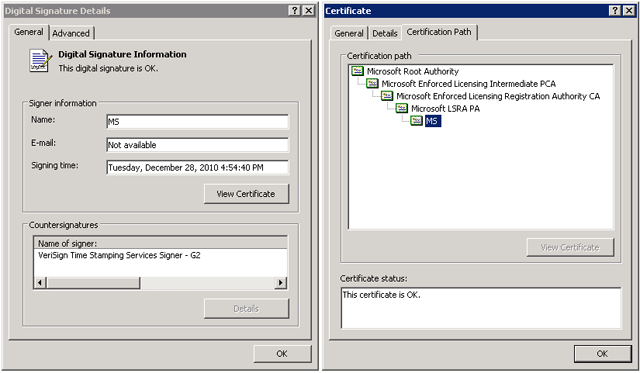
Flame components known as "Gadget" and "Munch" allow Flame operators to mount a man-in-the-middle attack against computers connected to a local network that hosts at least one machine already infected by the malware, Kaspersky Lab expert Alexander Gostev wrote in a blog post published Monday. By exploiting weaknesses in Microsoft's Terminal Server product—and poor key-management decisions made by Microsoft engineers—the Flame architects were able produce cryptographic seals falsely certifying that their malicious wares had been produced by Microsoft.
Microsoft issued an emergency update on Sunday that added three certificate authorities to its list of untrusted certificates, but it's unclear how useful such measures will be at repairing the damage. Company officials have yet to acknowledge the susceptibility of the update process or to provide guidance for customers whose networks may already be compromised. A representative with Microsoft's outside PR firm told Ars that Microsoft "doesn't have anything further to share at this time," and referred reporters to a series of blog posts that didn't address these unanswered questions.
According to Kaspersky's Gostev, Flame attackers have been using the same fraudulent Microsoft certificates to spoof the company's widely used Windows update mechanism. Other researchers quickly weighed in on the enormity of the attack.
"Having a Microsoft code signing certificate is the Holy Grail of malware writers," Mikko Hypponen, chief research officer of antivirus provider F-Secure, blogged on Monday. "This has now happened."
A separate blog post published Monday by Symantec researchers further catalogs the enormous data collection capabilities of Flame. The sheer breadth of functionality and size sets it apart," Symantec researchers wrote. "Even describing it as an industrial vacuum cleaner does not do it justice."
The flame modules are able to bypass the legitimate Windows update by setting up a fake server named MSHOME-F3BE293C on networks that host an infected machine. When machines attached to the network run software that advertises itself as an official Microsoft update, the fake server delivers the Flame malware instead, causing those machines to also become infected.
Right now, Microsoft is using its emergency update process to push a patch that mitigates a Windows threat that can hijack the emergency update process. No doubt, end users should install the patch as soon as possible. But it's naive to think this out-of-band fix will repair the damage done to networks already hit by Flame, at least until Microsoft representatives provide additional guidance.
reader comments
38