Oracle has declined to patch a critical vulnerability in its flagship database product, leaving customers vulnerable to attacks that siphon confidential information from corporate servers and execute malware on backend systems, a security researcher said.
Virtually all versions of the Oracle Database Server released in the past 13 years contain a bug that allows hackers to perform man-in-the-middle attacks that monitor all data passing between the server and end users who are connected to it. That's what Joxean Koret, a security researcher based in Spain, told Ars. The "Oracle TNS Poison" vulnerability, as he has dubbed it, resides in the Transparent Network Substrate Listener, which routes connections between clients and the database server. Koret said Oracle learned of the bug in 2008 and indicated in a recent e-mail that it had no plans to fix current supported versions of the enterprise product because of concerns it could cause "regressions" in the code base.
"This is a 0day vulnerability with no patch," Koret wrote in a post published Thursday to the Full-disclosure security list. "Oracle refuses to patch the vulnerability in *any* existing version and Oracle refuses to give details about which version will have the fix."
He told Ars he was concerned the vulnerability may come under attack after he inadvertently released bug details and proof-of-concept exploit code a day earlier. Koret said he published that report after Oracle earlier this month publicly recognized him by name for his report and later provided him with a tracking number that indicated the contribution related to his discovery of the TNS Poison vulnerability.
Only after Koret published his detailed advisory did he learn that the bug wasn't being removed from current versions of Oracle Database. Rather, he said, an e-mail he received from a member of Oracle's security team indicated only future versions of the enterprise package would be fixed to remove the bug. The message went on to suggest current versions would not be updated because of concerns they might be corrupted by the changes.
"The fix is very complex and it is extremely risky to backport," the Oracle e-mail stated. "This fix is in a sensitive part of our code where regressions are a concern. Customers have requested that Oracle not include such security fixes into Critical Patch Updates that increases [sic] the chance of regressions."
When Koret pressed Oracle to explicitly say if engineers planned to allow the bug to remain in current versions, an Oracle employee responded:
"To protect the interest of our customers, we do not provide these level of details (like versions affected) for the issues that are addressed as in-depth. The future releases will have the fix."
Oracle representatives didn't respond to multiple e-mails seeking comment for this article.
Oblivious to attack
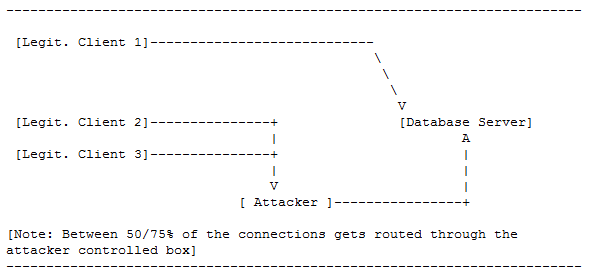
A TNS Listener feature known as remote registration dates back to at least 1999 with version 8i of the Oracle Database. By sending a simple query to the service, an attacker can hijack connections legitimate users have already established with the database without the need of a password or other authentication. From then on, data traveling between legitimate users and the server pass through the connection set up by the attacker.
"The attacker owns the data as almost all the connections go through the attacker's box," Koret wrote in his detailed advisory. "The attacker can record all the data exchanged between the database server and the client machines and both client and server will be oblivious of the attack." Attackers can also use the connection to send commands to the server that instruct it to add, delete, or modify data. Attackers could also exploit the bug to install rootkits that take control of the server itself, he told Ars.
"Regarding the server side, yes, it can be used to install, for example, a database rootkit, if a DBA (database administrator) connection is captured in the man in the middle (or by capturing a normal user's session and then using a privilege escalation vulnerability, something not that hard)," he wrote in an e-mail to Ars. "Also let's say that an attacker finally gained DBA access to the database: (s)he then is capable of executing operating system commands with the privileges of the running user." On servers running Microsoft Windows, the Oracle Database runs as a Local System, giving an attacker significant control. Systems running Unix-based operating systems have more limited control, but attackers could possibly exploit other vulnerabilities to elevate those privileges.
TNS Listener can be set up to listen for connections over the Internet, Koret warned. This makes it possible for the vulnerability to be exploited remotely over the Internet. Fortunately, Koret said, such Internet-wide configurations are rare. In those cases, attackers would require access to the private network hosting the database server.
The lack of a fix is compounded by Koret's inadvertent disclosure of detailed instructions for exploiting the vulnerability. Making matters worse, Oracle has yet to confirm or deny Koret's claim that there will never be a fix for current versions of the database product.
That means it's up to Oracle customers to lower their exposure to the vulnerability. Koret's initial post includes a list of "possible workarounds." One such technique involves setting up load balancing on client machines and updating their configuration to include a full list of Oracle RAC nodes. Another possible mitigation is to update the protocol.ora or sqlnet.ora files on vulnerable servers to check for valid nodes. Customers who have bought the Oracle Advanced Security feature can also lower the risk of attack by mandating the use of secure sockets layer authentication between clients and servers.
On Monday afternoon, Oracle released its own list of mitigations and strongly urged customers to implement them right away.
"Considering that the technical details of vulnerability CVE-2012-1675 have now widely been distributed, Oracle highly recommends that customers make the configuration changes documented in the above mentioned My Oracle Support Notes as soon as possible," Oracle's Eric Maurice blogged. "Customers should also feel free to contact Oracle Support if they have questions or concerns."
Listing image by Image courtesy of Oracle
reader comments
44