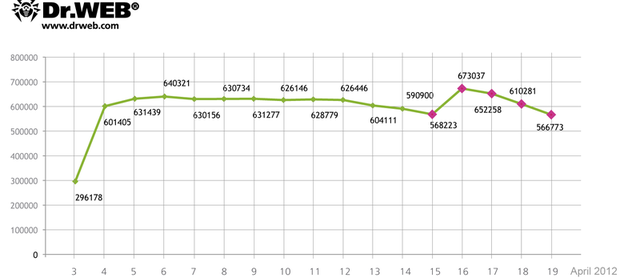
Analysis declaring the demise of the Flashback Mac backdoor has been greatly exaggerated, said researchers with a Russia-based antivirus firm, who on late Friday estimated there are 650,000 unique OS X machines currently infected by the malware.
The estimate by Doctor Web is in stark contrast to analysis provided Wednesday by Symantec, which showed the number of compromised systems had dropped from more than half a million to about 140,000. Following the release of the latest Doctor Web estimate, Symantec updated its post to say company researchers now believe their servers "are receiving limited infection counts" for the malware.
The revised numbers are the result of so-called sinkholes that researchers construct to act as surrogate command and control servers for hijacked machines. To give the Flashback botnet resilience against a takedown of the real command channels, the malware uses the current date, and certain code-embedded parameters, to dynamically generate alternate domain names the infected Macs report to. By registering the domains ahead of the Flashback operators, security researchers are able to create benign control servers that can prevent the bots from receiving harmful commands and can also conduct reconnaissance on the targeted malware.
According to Doctor Web, different sinkholes used by different researchers have returned vastly different statistics about the machines reporting to them. Mac antivirus provider Intego has concurred with those findings, at least in part, it said, because some domain name system lookup services are blocking the IP resolution of some of the domains used by the sinkholes.
"The effect here is that the Macs are still infected, but they will not be able to contact the command and control servers, and especially, cannot be counted by sinkholes," Intego researcher Peter James wrote in a post published on Friday morning.
Both Doctor Web and the update from Symantec went on to say a specific sinkhole at IP address 74.207.249.7 was failing to close TCP connections after being contacted by infected machines.
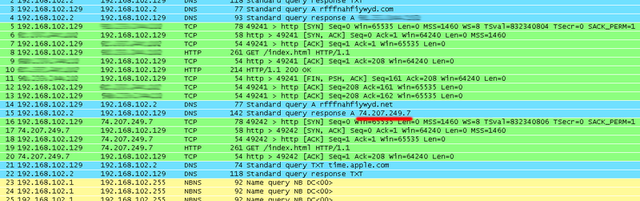
"As the result, bots switch to the standby mode and wait for the server's reply and no longer respond to further commands," Friday's post from Doctor Web stated. "As a consequence, they do not communicate with other command centers, many of which have been registered by information security specialists."
The post estimates that a total of 817,879 bots have been a part of the botnet at one time or another since Doctor Web first started monitoring it on April 4. On Monday, 717,004 unique IP addresses and 595,816 Mac unique user IDs checked in. The number of IP addresses and UUIDs the following day were 714,483 and 582,405. And so, of the estimated infected Macs, "the number is still around 650,000," the post said.
The motives behind the Flashback operators remain murky, but researchers suspect the malware may be involved click fraud scams, since it often alters query results retuned by search engines. The malware first spread by masquerading as an update for Adobe's Flash player, and more recently by exploiting a critical Java vulnerability that Apple was slow to patch. Researchers from Kaspersky have said that starting in late February, tens of thousands of sites running WordPress began pushing the malware, suggesting that attackers may have exploited a vulnerability in the blogging tool to mass infect the sites with exploits. On late Friday, WordPress issued a security update here.
Over the past two weeks, Apple and a variety of third-party software providers have offered free tools to diagnose and cure Flashback infections. As researchers started seeing fewer bots reporting to their sinkholes, they assumed the decline was the result of end users patching and repairing their Macs. Now, those assumptions are open to debate.
Said Intego's James: "The realization now that the actual number of infected Macs is a multiple of the numbers cited recently in the press suggest that as many Macs are disinfected others are being infected."
Listing image by Photograph by st.drweb.com
reader comments
94