A botnet that redirected clicks from millions of PCs has been shut down by Microsoft and Symantec, at least for the moment. Based on the fraudulent traffic generated by the Bamital botnet, the two companies estimate that its operators netted more than $1 million a year by redirecting unsuspecting computer users to websites they didn't intend to go, cashing in on the traffic with online advertising networks.
Acting on a court order they obtained from the US District Court in Alexandria, technicians from the two companies—accompanied by federal marshals—showed up at two data centers today to take down the servers controlling the Bamital botnet. A server in an ISPrime data center in Weehawken, New Jersey was seized, while the operators of a LeaseWeb data center in Manassas, Virginia voluntarily shut down a server at the company's headquarters in the Netherlands. LeaseWeb is providing an image of that server to Microsoft and Symantec. "These servers were command and control servers and were also absorbing the malicious traffic the botnet was creating," said Vikram Thakur, principal security response manager at Symantec in an interview with Ars.
Richard Boscovich, Microsoft's general counsel, said that while the malware had been identified as far back as 2011, nailing down the exact servers they needed to go after took some time. "The malware was morphing back and forth, so it made it difficult to identify the targets," he said. But when the botnet stabilized a few months ago, "it offered a window of opportunity to go after them. The legal portion took about two months."
Based on forensic evidence collected from infected computers by Symantec and Microsoft, there have been several generations of Bamital, with activity dating back at least three years. Early variants of the malware attacked users' Web browsers with HTML injection. "They injected an iframe into every page," Thakur said, "so whatever page loaded also loaded content from the bad guys."
In later variants of Bamital, the malware simply redirected any click on a search page to the botnet's own servers, which in turn used HTML redirects to feed the victims' traffic into an advertising network. That network acted as a clearinghouse for other advertiser networks, so a click could go through several sets of redirects before it actually landed on a website—and not the one the user expected.
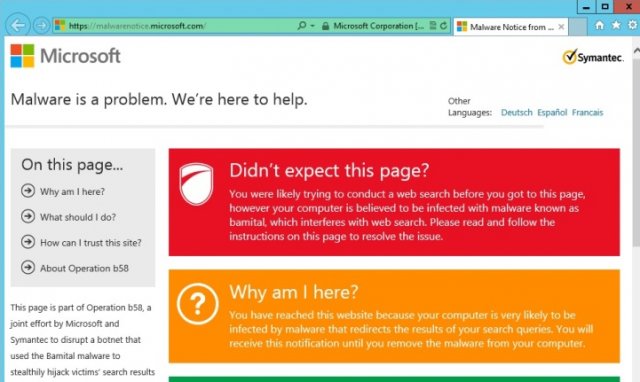
Because of the nature of Bamital, Microsoft is now in a position that's different from some of its previous botnet takedowns—it has a direct line to victims of the malware. "One of things we're doing a little differently in this case is we're doing direct victim notification," Boscovich said. Users with systems infected by Bamital will now be redirected to a Microsoft webpage offering tools to help remove the Bamital malware—as well as any other malware that's out there.
"There are AV signatures out there for this malware already," Boscovich said. "They may have an OS that's unpatched or antivirus software that's outdated. We're taking control of the command and control network so that every time someone types in a search query, they're going to get redirected to a page directly by Microsoft."
Thakur said that the Bamital malware was initially delivered by a combination of methods, including in packages over peer-to-peer filesharing networks disguised as other content. But the majority of systems infected were the victim of "driveby downloads" from websites configured with malicious software intended to exploit browser security flaws. "We have evidence of [the botnet operators] polluting search engine results for certain search terms with links to servers with exploits," he said.
As new variants of the botnet were developed, the operators made efforts to "upgrade" systems they had already infected. "But along the way they seemed to have left behind a number of people," Thakur said. The older servers that had been used with previous versions of the malware appear to have been abandoned as well.
In 2011, Microsoft and Symantec were able to monitor the traffic going to one of the botnet's servers. "We got back data that showed that 3 million clicks were being hijacked by that server on a daily basis," Thakur said. Based on a conservative estimate of a payment for one-tenth of a percent of the advertising value for each click, the companies determined the fraud ring was pulling in over $1 million a year from advertising networks. "And it could have been 2 or 3 times that much," he said.
The advertising networks connected to Bamital themselves may be completely fraudulent. They acted as clearinghouses for the traffic and resold it to other, legitimate advertising networks and affiliate programs. "Bamital went through several ad networks before it even displayed content," Thakur said. "It was super convoluted."
Microsoft and Symantec are hoping the data obtained through the seizure of the server in New Jersey will help them get a better understanding of the underground ecosystem of advertising networks that drives botnets like Bamital. But it's too early to tell if it will help catch the actual perpetrators. "We still have to go through the evidence," Boscovich said, but he noted that Microsoft had some success in the past in identifying botnet operators, as it did with Kelihos.
reader comments
65