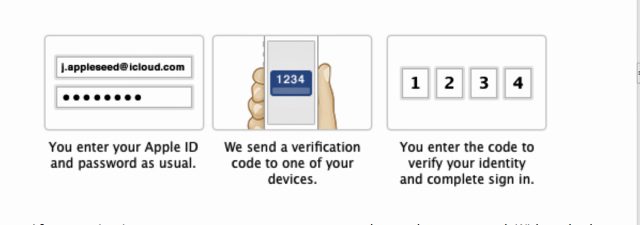
If you think your pictures, contacts, and other data are protected by the two-step verification protection Apple added to its iCloud service in March, think again. According to security researchers in Moscow, the measure helps prevent fraudulent purchases made with your Apple ID but does nothing to augment the security of files you store.
To be clear, iCloud data is still secure so long as the password locking it down is strong and remains secret. But in the event that your account credentials are compromised—which is precisely the eventuality Apple's two-factor verification is intended to protect against—there's nothing stopping an adversary from accessing data stored in your iCloud account. Researchers at ElcomSoft—a developer of sophisticated software for cracking passwords—made this assessment in a blog post published Thursday.
"In its current implementation, Apple’s two-factor authentication does not prevent anyone from restoring an iOS backup onto a new (not trusted) device," ElcomSoft CEO Vladimir Katalov wrote. "In addition, and this is much more of an issue, Apple’s implementation does not apply to iCloud backups, allowing anyone and everyone knowing the user’s Apple ID and password to download and access information stored in the iCloud. This is easy to verify; simply log in to your iCloud account, and you’ll have full information to everything stored there without being requested any additional logon information."
He continued:
"In ElcomSoft's opinion, this is just not the right way to do this from a security point of view. iCloud has been exploited in the past (see Norwegian Teenagers Hacking iCloud Accounts) and will be exploited in the future."
To be fair to Apple, there's nothing in the company's FAQ for two-factor verification that says or implies user data is protected by the new measure. Still, it was rolled out a few months after hackers exploiting security loopholes in online services from Amazon and Apple wiped out the entire digital life of Wired editor Mat Honan. Given the timing of Apple's two-factor introduction, it wouldn't be surprising if some customers believed it prevented the same kind of thing from happening to them in the event a hacker was able to exploit similar vulnerabilities.
According to ElcomSoft's Katalov, the new measure may not stop the types of attacks that visited Honan. While it prevents attackers from resetting a user's iCloud password, it doesn't keep them from copying or deleting files stored in an account. Once the password locking it down has been compromised—and again, this is precisely the scenario two-factor authentication is designed to mitigate—an attacker can restore backed up iPhone or iPad data to a new device. Unless Apple has behind-the-scenes protections it hasn't talked about, the attacker then has the ability to gain a considerable amount of control over the files, including deleting them forever. That sounds a lot like the hack that hit Honan last year.
"To me the story here is all about Apple offering a 2FA [two-factor authentication] solution that doesn't really add much extra security for you (files, documents etc), but it protects them (and you) from unauthorized money transactions and changes to your account," Per Thorsheim, a security consultant in Oslo, Norway, wrote in an e-mail to Ars. "People are not made aware of this at all, and it will be a false layer of security when people enable 2FA and put sensitive and secret documents into iCloud."
He continued:
"People EXPECT a 2FA solution to add additional security in order to protect their data, but contrary to Dropbox & Google, Apple doesn't really do that. It's the 'weakest' 2FA solution launched so far by the big and well-known services, it will only add an additional layer of false security to people's minds, which may have dangerous results."
Convenience as the enemy of security (and vice versa)
But people also expect it to be easy to log in to their accounts and often become furious when they can't access their data. The lack of any two-factor authentication protecting data stored in iCloud accounts is probably a conscious decision by Apple engineers to avoid the kinds of kluges found on other sites that offer two-factor protection. Google often uses application-specific passwords to protect user data because many programs—IMAP compliant e-mail clients, for instance, or Adobe's Lightroom application—aren't currently capable of accepting verification codes. Application-specific passwords help lessen the damage that results when an attacker obtains a Google user's password. But the protection comes at a cost.
"In order for Google to cover all their bases, Google two-factor can sometimes be a pain to use," Dan Wallach, a professor in the computer science department of Rice University, told Ars. "Google has done such a good job on security that now they have a usability problem."
Apple engineers, it seems, have opted to err on the other side by sacrificing some protection in favor of giving users more convenience. Depending on how closely iCloud users have read Apple's documentation and tested the way two-factor verification protects their accounts, this may or may not be new information. Still, security researchers said ElcomSoft's analysis is valuable.
"It's a worthwhile discovery," said Jon Oberheide, CTO of Duo Security, a company that delivers two-factor authentication services to business customers. "It's good for people to know and understand that their account is not 100-percent protected by this new feature that rolled out. But I don't think it's an unaddressable limitation, and to be fair to Apple, I don't know if this was ever intended to protect this model."
reader comments
77